Why is Incident Response in Cybersecurity so Important?
- Home
- Why is Incident Response in Cybersecurity so Important?

Here’s the thing most legal teams get wrong: they treat cyber incidents like IT problems.
They’re not. Not anymore.
In a security breach, the first 2-3 days determine not just how quickly your systems recover. They determine whether you’re looking at regulatory fines, mandatory client notifications, or even litigation down the road.
Incident response in cybersecurity has emerged as one of the most legally significant processes in any organization, and yet, most legal departments remain on the sidelines until someone else delivers them the damage report.
That’s a problem. So let’s break things down.
What Does Incident Response Actually Mean?
Incident response is the plan of action that an organization has in place when a cybersecurity incident happens. It is the game plan, not the cleanup crew.
It includes everything from realizing that something has gone wrong, through containing the problem, to understanding what happened, and finally returning to normal.
But here is what makes it more than just a technical exercise: every single step in the process has legal ramifications.
Did the breach expose personal data? You might owe notification letters.
Was client data involved? There are contractual obligations at play.
Are there regulatory deadlines? State breach notification laws vary, and some are brutally short.
A wrong response not only costs money. It can lead to missed deadlines, failed compliance, and lawsuits that could have been avoided with a better plan in place.
This is exactly why incident response in cybersecurity is no longer just an IT conversation. It’s a legal one.
Why Legal Teams Can't Afford to Ignore This
Let’s be direct. If your organization doesn’t have a clear incident response plan that includes legal, you’re flying blind when it matters most.
Here’s what tends to happen in practice:
The IT or security team detects something suspicious. They start investigating internally. By the time legal gets looped in, critical decisions have already been made. Sometimes, decisions that affect your legal exposure significantly.
Communications have gone out. Evidence may have been altered or lost. Notification timelines have started ticking, whether anyone realized it or not.
This is one of the most common and costly mistakes we see across law firms and corporate legal departments alike.
The legal team needs to be involved from the very start. Not after the fact. Not once someone realizes there’s a compliance angle. From. The. Start.
That means incident response plans need to be written with legal input baked in, not bolted on later.
Incident Response in Cybersecurity: The Legal Obligations You Need to Know
This is where it gets serious. The legal requirements you face after a breach aren’t universal; they shift based on your industry and where your clients or business are located. In some cases, obligations apply the instant a breach is detected, and you’re required to act right away.
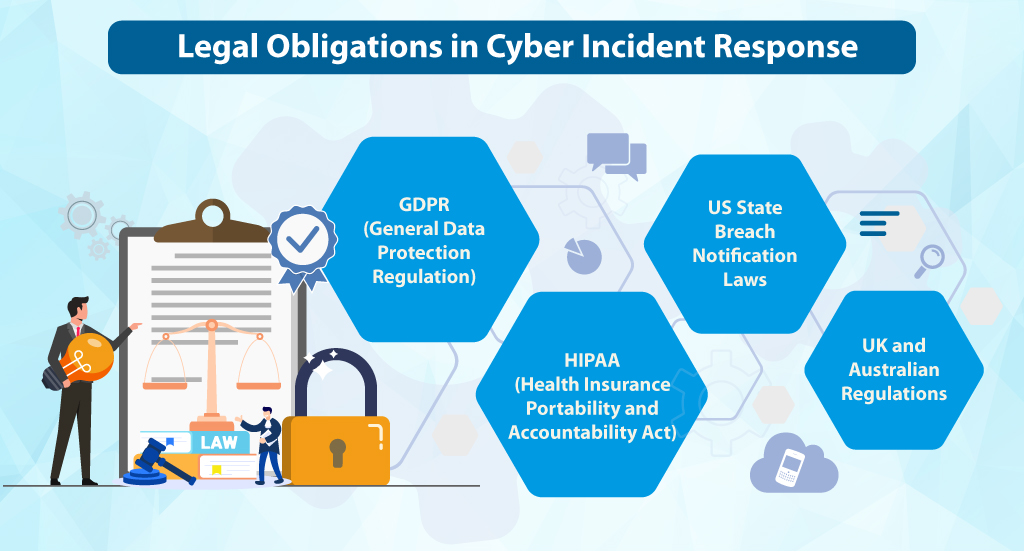
GDPR (General Data Protection Regulation)
If your business mishandles the personal data of EU citizens, GDPR gives you just 72 hours from the moment you spot the breach to report it to the data protection authority. Miss that window, and you risk penalties as steep as 4% of your global annual revenue.
HIPAA (Health Insurance Portability and Accountability Act)
If you are a healthcare business operating in the US, you have to notify the affected individuals of a breach within 60 days of the breach being detected. However, the investigation will determine if a breach has actually occurred. This clock begins ticking the moment you realize something is not right.
US State Breach Notification Laws
All 50 US states have their own breach notification laws. The timelines, definitions of “breach,” and requirements differ. Some states require notification within 30 days. Others give you 60. Knowing which laws apply to your situation is a full task in itself.
UK and Australian Regulations
The UK’s post-Brexit data protection framework and Australia’s Notifiable Data Breaches scheme both have their own reporting requirements. If your firm or your clients have operations in these regions, those rules apply too.
The bottom line: incident response isn’t just about stopping an attack. It’s about meeting legal deadlines, preserving evidence, and making sure your organization stays on the right side of the law.
The Phases That Matter Most From a Legal Perspective
Most cyber incident response frameworks break down the process into five or six phases. We’re going to focus on the ones that matter most to legal teams.
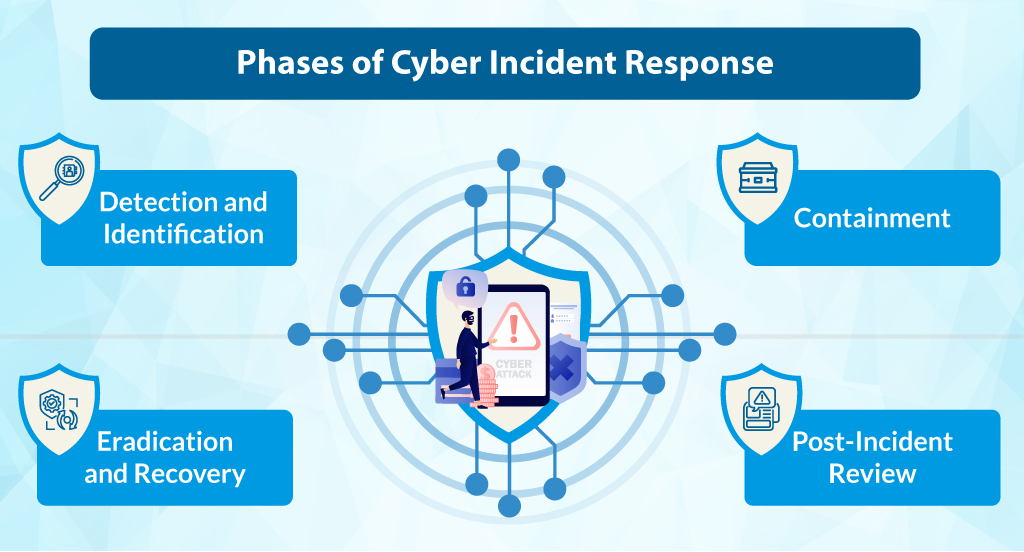
Detection and Identification
This is ground zero. Someone, whether it’s an automated system or a person, flags that something is off. The moment this happens, legal obligations may already be in motion. Time-sensitive notification requirements don’t care whether your IT team has finished their internal review.
Containment
The objective in this case is to prevent the damage from spreading. However, from a legal perspective, containment also involves the preservation of evidence. If your team is wiping systems or overwriting logs to “clean up” the mess, you could be destroying information that is essential for regulatory investigations or litigation down the line.
Eradication and Recovery
Once the threat is dealt with, the focus shifts to getting back to normal. For legal, this phase is about documentation. What happened? What data was affected? What actions were taken, and when? This information becomes the backbone of your notification letters, regulatory filings, and any legal defense down the line.
Post-Incident Review
This is the phase most teams rush through, but they shouldn’t. A thorough review doesn’t just help you improve your response next time. It also helps you build a defensible record showing that your organization took the incident seriously and responded responsibly.
How LPOs Play a Role in Cyber Incident Response
This is where things get interesting for firms that work with legal process outsourcing providers.
When a cyber incident hits, the volume of work that lands on a legal team can be staggering. Notification letters need to go out, often to thousands of individuals. Documents need to be reviewed. Evidence needs to be preserved and organized. Regulatory filings need to be drafted accurately and on time.
That’s where LPOs come in. We handle the high-volume, detail-heavy work that legal teams don’t have the bandwidth to manage during a crisis. Document review, drafting support, and compliance workflows are exactly the kinds of tasks that benefit from outsourcing during an incident.
The key is having that relationship built before an incident happens. Not during one.
Common Mistakes Legal Teams Make During Cyber Incidents
A few patterns keep showing up, and they’re worth flagging:
Waiting too long to get involved: Legal needs to be in the room from day one. Every hour of delay increases risk.
Treating it as purely a technical issue: It’s not. The legal, regulatory, and reputational stakes are just as real as the technical ones.
Not preserving evidence properly: If you need to defend your response later in court or to a regulator, you need a clear, clean trail of what happened and what you did about it.
Failing to map out notification requirements in advance: When you’re in the middle of a crisis, figuring out which laws apply and what the deadlines are is the last thing you want to be doing. That work should be done ahead of time.
The Bottom Line
Incident response in cybersecurity used to be something only IT teams worried about. That ship has sailed.
For legal departments, law firms, and the LPOs that support them, this is now front and center. The regulations are tighter. The timelines are shorter. The consequences of getting it wrong are bigger.
The good news? You don’t need to figure this out alone. Building a solid incident response plan with legal involvement is one of the smartest things your organization can do right now. Before you need it.
At Aeren LPO, we work behind the scenes supporting law firms and legal teams with the high-volume work that keeps operations running smoothly. From document review to compliance workflows, we handle the details so your team can focus on what matters most.

