The Regulatory Domino Effect of a Data Breach & How to Stay Ahead
- Home
- The Regulatory Domino Effect of a Data Breach & How to Stay Ahead

A data breach doesn’t end when you patch the vulnerability or notify affected parties. That’s actually when your real problems begin.
What follows is a cascade of regulatory scrutiny that can span multiple jurisdictions, trigger overlapping compliance requirements, and consume resources for months, sometimes years. The notification is just the starting gun. The actual race involves making your way through regulatory bodies, each operating on different timelines with different expectations, while simultaneously managing forensic investigations, remediation efforts, and increasingly complex legal obligations.
Why Data Breaches Trigger Multiple Regulatory Responses
When sensitive data is compromised, you’re not dealing with a single regulator or a single set of rules. You’re dealing with a complex web of overlapping authorities, each with its own timelines, requirements, and penalties.
Here’s what catches most organizations off guard: regulatory responses don’t happen in sequence. They happen simultaneously. While you’re responding to one agency’s investigation, another is launching theirs. While you’re implementing remediation for one jurisdiction, you’re facing entirely different requirements from another.
The GDPR requires notification within 72 hours. State attorneys general have their own timelines. Industry-specific regulators, such as HIPAA’s Office for Civil Rights, or financial services regulators, add another layer. And if your customer base spans multiple jurisdictions, which most companies do, you’re managing compliance obligations that often contradict each other.
This gets even more complicated when you consider that different jurisdictions define breach triggers differently. Is it when you discover the vulnerability? When you confirm that the data was accessed? When you complete your investigation? Each answer can shift your notification deadlines by days or weeks.
Also Read: The First 72 Hours of a Data Breach: What Really Matters for Legal Response Teams
The First Domino: Mandatory Disclosure Requirements
The moment you discover a breach, the clock starts ticking on multiple notification requirements. But it’s not as simple as sending out alerts.
Different jurisdictions have their own ways of defining “personal data”. In California, the CCPA establishes additional categories of personal data, including biometric information and internet activity. The GDPR defines a broader category than the CCPA does, and in some cases, a notification may not be required under state law unless there is a reasonable probability of harm. Others mandate it regardless. Texas has a different requirement for reporting than New York. Australia’s NDB system is different from Canada’s PIPEDA requirement for reporting.
This creates a practical nightmare for any organization operating across borders. You need to determine which jurisdictions apply, what data elements were exposed, who needs to be notified, and in what timeframe, all while conducting a forensic investigation to understand the breach’s full scope.
Here’s the kicker: if you get the notification wrong, too late, too vague, or to the wrong parties, you’re looking at additional penalties on top of the breach itself. Some jurisdictions penalize inadequate notifications almost as severely as the underlying security failure.
The Compliance Cascade That Follows

Once regulators have received your notifications, they will likely conduct compliance inquiries into your organization. These inquiries are far from merely a “check the box exercise.” They include a complete assessment of your organization’s security stance and may extend over several years.
State attorneys general will want to know why your security measures failed. They’ll examine your vendor management practices, your employee training programs, and your cyber incident response plans. If you’re handling healthcare data, OCR will conduct its own HIPAA investigation. If you’re in financial services, expect inquiries about your compliance with Gramm-Leach-Bliley Act requirements, state banking regulations, and potentially SEC oversight.
Regulators will investigate differently depending on their approach to compliance and the industries they cover. For example, certain regulators might request technical documents detailing the company’s network, including its architecture, access logs, known vulnerabilities, and knowledge of key people, from the IT team through to senior management. Other regulators may focus more on whether a company maintained sufficient safeguards before an attack. In contrast, others may be more interested in the company’s response and remediation efforts after an attack.
The challenge isn’t just responding to these inquiries; it’s doing so while maintaining business operations. You can’t pause revenue-generating activities because you’re dealing with regulators. But you also can’t afford to botch your regulatory responses, because those failures compound your legal exposure.
The Hidden Costs Beyond Direct Penalties
Everyone focuses on the headline penalties, the millions in fines that major breaches generate. But those aren’t the costs that impact most organizations.
The real financial impact comes from the operational disruption. Your legal team is now spending weeks responding to regulatory inquiries instead of focusing on strategic initiatives. Your IT team is implementing new security controls, conducting audits, and remediating vulnerabilities. Your leadership is in meetings with regulators, insurers, board members, and concerned customers.
Meanwhile, your customers are asking difficult questions. How was their data exposed? What are you doing to prevent it from happening again? Should they take their business elsewhere?
For many organizations, reputation damage dwarfs any regulatory penalty. Customer churn accelerates. New customer acquisition becomes more expensive. Partners become hesitant. Investors grow concerned. And here’s what makes it worse: your competitors will use your breach as a selling point, positioning themselves as the secure alternative.
Then there’s the litigation. Class action lawsuits follow major breaches almost automatically now. Even if you ultimately prevail, the legal costs are substantial. Discovery is expensive. Expert witnesses are expensive. Settlements are expensive.
Industry-Specific Complications
As you enter into the field of Healthcare, Financial Services, or Insurance, you will find that the Regulatory Environment is going to be exponentially complicated because each individual industry has specific Regulatory Requirements, which are going to add on top of the overall Data Protection Regulations.
HIPAA requires notification, but it also requires that an organization perform a risk assessment, formulate a mitigation plan, and, in many cases, an organization will also be required to formulate a multi-year corrective action plan, which the OCR monitors. Financial services firms face scrutiny from multiple regulators simultaneously: state banking authorities, the SEC, FINRA, the CFPB, and the Federal Reserve each have jurisdiction over different aspects of data security.
In healthcare, even relatively small breaches can trigger audits that examine your entire compliance program. OCR has significantly expanded its audit program, and breaches often trigger comprehensive compliance reviews.
Manufacturing companies dealing with export-controlled technical data face additional complications under ITAR or EAR regulations. A data breach involving controlled technical data can trigger State Department or Commerce Department investigations in addition to standard privacy regulators.
Technology companies face scrutiny from the FTC, which has increasingly used its Section 5 authority to pursue companies for inadequate security practices. The FTC has its own angle. They go after security failures as basically lying to customers or running a sketchy business, which gives them ways to come after you that have nothing to do with typical data protection rules.
The Multi-Jurisdictional Puzzle
One of the most challenging aspects of the regulatory domino effect is managing conflicting requirements across jurisdictions. What GDPR requires might conflict with what California law mandates. Canadian requirements differ from Australian ones. UK post-Brexit regulations are diverging from EU standards.
Some jurisdictions require detailed disclosure about what data was compromised. Others restrict what you can disclose to avoid tipping off potential criminals. Some require notification to regulators before notifying affected individuals. Others mandate the opposite sequence.
The timeline alone is enough to give you a headache. Got data from EU residents? You’ve got 72 hours to notify regulators. The problem? Your investigation probably won’t be done by then. So what do you do? Report what you know now and risk getting it wrong? Or wait until you’re sure about everything and potentially blow past the deadline?
These aren’t theoretical concerns. Organizations face these exact dilemmas during active breach responses. The decisions you make in those first 72 hours can determine whether you’re looking at minimal penalties or regulatory enforcement actions.
Building a Proactive Defense Strategy
The best way to handle the regulatory domino effect is to prevent the first domino from falling. But since no security is perfect, the second-best approach is building resilience into your operations before an incident occurs.
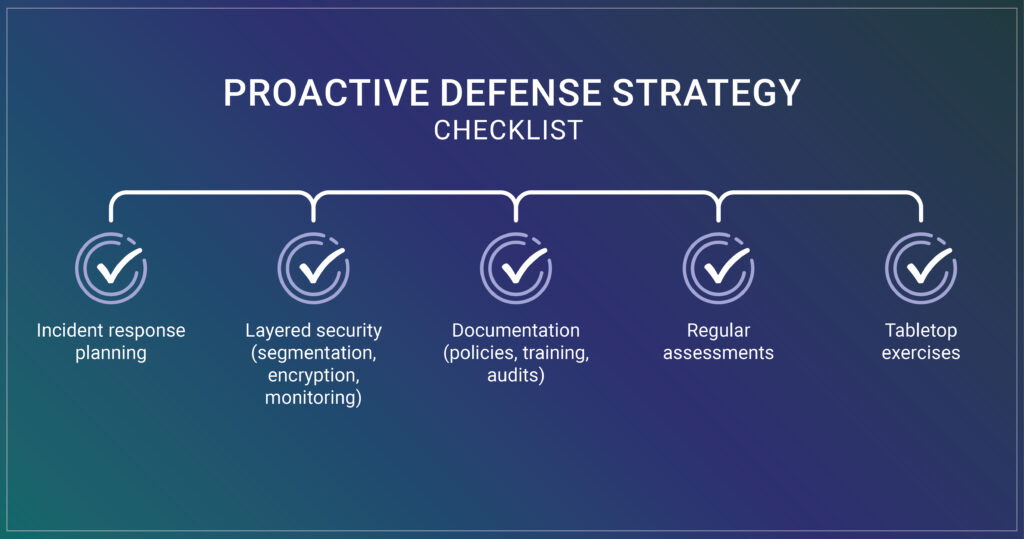
Make a detailed cyber incident response plan for your organization that includes provisions for incidents that cross jurisdictions. Your incident response plan needs to answer some basic questions: Who decides when to notify people? Who talks to the regulators? Who handles freaked-out customers? Who’s running the investigation? Don’t wait until you’re in the middle of a crisis to figure this out. Assign these jobs to specific people now, and actually practice running through scenarios so everyone knows what they’re doing when things hit the fan.
Your security plan should use layered security methodologies, accounting for the fact that security breaches will occur, and implementing systems and processes to limit their effect. Network segmentation, robust access controls, encryption at rest and in transit, and continuous monitoring are the differences between a contained incident and a catastrophic exposure.
Many companies do not put a great deal of emphasis on their documents, but they clearly show government regulators that your organization took security seriously prior to your breach. Your policies, training records, audit logs, vulnerability assessments, and risk management frameworks become your primary defense in regulatory proceedings. If you can demonstrate that you maintained reasonable security practices appropriate to the data you hold, penalties tend to be significantly lower.
Regular security assessments help identify vulnerabilities before attackers do. Penetration testing, vulnerability scanning, and security audits should be routine, not reactive. When regulators investigate, they’ll look at when you last assessed your security posture and whether you addressed identified weaknesses.
Vendor Management as a Critical Control Point
Third-party vendors create both opportunities and vulnerabilities. Your cloud providers, software vendors, and service providers all may have access to sensitive data. If there is a compromise of their data security, in most instances, it is still your responsibility to notify affected individuals and be in compliance with governmental regulations.
This is why vendor due diligence can’t be a one-time checkbox exercise. You need continuous monitoring of vendor security practices, regular audits of their controls, and contractual provisions that clearly define breach notification responsibilities and liability allocation.
The reality is that many breaches originate in the vendor ecosystem. The Target breach came through an HVAC vendor. Numerous healthcare breaches have originated with business associates. When regulators come knocking, they won’t just look at your own security measures; they’ll dig into how you handled risk from the companies you work with.
Make sure your vendor contracts spell out the important stuff: how quickly they need to tell you about problems, whether they’ll help with investigations if something goes wrong, and who’s on the hook for any fines. Without clear contractual language, you may find yourself in disputes with vendors about who’s responsible for what when a breach occurs.
The Path Forward
The regulatory response to data breaches will only intensify. New privacy laws are being enacted constantly. Virginia, Colorado, Connecticut, and Utah have all passed comprehensive privacy legislation in recent years. Look, enforcement agencies aren’t messing around anymore, penalties keep climbing, and trying to navigate different rules across countries is getting messier by the day.
But here’s the thing: no one has perfect security. It just doesn’t exist. The companies that make it through breaches aren’t the ones who never get hit, they’re the ones who know how to handle things when something actually goes wrong.
Create your compliance framework when it is still in development. Create a relationship with the relevant regulatory authorities (i.e., the people who enforce compliance laws) before you must notify them when you experience a breach. Train your employees/processes to respond to incidents before they occur (i.e., ensure your employees know what to do when the time comes). Consistently document your security practices (i.e., in the normal course of business, not only in response to an event). Conduct tabletop exercises that simulate regulatory response alongside technical response.
The regulatory domino effect is real, complex, and expensive. But with proper planning, robust security practices, and a clear understanding of your compliance obligations across all relevant jurisdictions, it’s manageable. The question isn’t whether you’ll face regulatory scrutiny, it’s whether you’ll be ready with the perfect cyber incident response when that scrutiny comes.
FAQ’s
- Mailchimp - For managing email marketing campaigns.
- Slack - For collaboration individual or team members easily.
- WhatsApp - For direct messaging with our customer support team inbox.

