How Data Breach Response Failures Damage Businesses
- Home
- How Data Breach Response Failures Damage Businesses

By the time a breach is “contained,” the real risk usually begins.
The intruder is out. Systems are back online. Dashboards look green again. Technically, the incident appears closed. Legally and financially, it is only starting.
Months later come the regulatory notices. Then the shareholder questions. Then, the customer attrition never quite reverses. In many cases, the fines and legal exposure outweigh the cost of the intrusion itself. This is where boards and leadership teams often misread the problem. They assume the breach is the crisis. It is not. The crisis is the data breach response.
Under modern privacy and cybersecurity regimes, the focus has shifted. Regulators, courts, and insurers are less concerned with whether an attack occurred and far more concerned with how the organization behaved once it knew about it. Speed of escalation. Quality of judgment. Preservation of evidence. Accuracy of disclosures. Internal control. These are governance tests, not technical ones.
Containment is an IT outcome. Liability is a leadership outcome.
What a Data Breach Response Team Actually Is
A cyber incident response team is not a project group. It is a temporary governing body.
For a short, intense period, it must exercise coordinated authority across technology, law, compliance, operations, and communications. It must do so while facts are incomplete, attackers may still be active, and regulatory clocks are already running.
In functional terms, it must bring together:
- Cybersecurity and forensic specialists
- Legal counsel and data protection officers
- Compliance and risk leadership
- Executives with decision rights, not just titles
- Communications professionals who understand legal exposure
When these roles are unclear or when authority is fragmented, the organization does not merely become inefficient. It becomes vulnerable in the eyes of regulators and courts. Confusion is interpreted as a lack of control. Lack of control is interpreted as governance failure.
What makes this worse is that many organizations test this structure for the first time during a real breach. Reporting lines are debated. Decisions are deferred. Information is filtered. By the time alignment is achieved, statutory notification windows are already closing.
That is not a response capability. It is crisis improvisation.
💻 Watch our webinar on how the first 24 hours determine breach costs and how to mobilize your PR, legal, tech, operations, and leadership teams as one unified response force.
4 Fatal Data Breach Response Failures
Across regulatory investigations and litigation, the same breakdowns appear with striking consistency.1. Delay in detection and escalation
Weak monitoring and unclear escalation paths allow attackers to operate for extended periods. By the time the breach is discovered, the issue is no longer a discrete incident. It is a prolonged compromise with evidentiary, legal, and disclosure consequences that are far harder to manage.2. No clear decision authority
Without a documented cyber incident response framework, paralysis sets in. Security wants to shut systems down. Legal wants to preserve evidence and privilege. Compliance is tracking notification deadlines. Executives want certainty that does not yet exist. While these debates play out, the attacker may still have access, and regulators’ clocks continue to run.3. Fragmented internal communication
Critical facts reach legal and compliance too late. Executives receive sanitized summaries that understate severity. By the time the full picture is visible, disclosure strategies and investigative posture are already compromised.4. Failure to preserve forensic integrity
Logs are overwritten. Images are not captured. The chain of custody is incomplete. This weakens internal understanding and becomes a central issue in regulatory scrutiny. Inadequate evidence handling is routinely treated as proof that “appropriate organizational measures” were not in place.The Full Spectrum of Data Breach Response Damage on Businesses
 When a breach is handled poorly, the harm does not remain confined to the security function. It spreads, compounds, and eventually shows up across the balance sheet, the courtroom, and the market. What begins as a technical incident becomes an enterprise-wide liability.
When a breach is handled poorly, the harm does not remain confined to the security function. It spreads, compounds, and eventually shows up across the balance sheet, the courtroom, and the market. What begins as a technical incident becomes an enterprise-wide liability.
Operational and Financial Impact
Business disruption
Extended system outages and containment actions interrupt revenue, delay service delivery, and in some sectors bring operations to a complete halt. The longer the response drags on, the more customers and partners are forced to find alternatives.Loss of intellectual property
Weak containment and investigation can allow the exfiltration of trade secrets, product roadmaps, pricing strategies, and commercially sensitive negotiations. The commercial impact of such loss is often invisible at first, but permanent.Regulatory sanctions
Under regimes such as GDPR, fines can reach up to 4% of global annual turnover. Similar exposure exists under HIPAA and emerging state privacy laws. Penalties are frequently driven not only by the breach itself, but by delayed notification, poor documentation, and inadequate governance during the response.Civil litigation
Class actions, individual claims for negligence, and contractual disputes follow quickly. Discovery focuses heavily on internal communications, response timelines, and decision-making quality. Weak response processes often become the central theory of liability.Insurance consequences
Carriers reassess risk after a failed response. Premiums rise, coverage narrows, exclusions expand, and in some cases, policies are withdrawn altogether, increasing long-term operating risk.Reputational and Long-Term Consequences
Erosion of trust
Customers rarely distinguish between being hacked and being mishandled. A slow, opaque, or inconsistent response undermines confidence in the organization’s ability to safeguard data and meet its legal obligations.Market confidence impact
Public companies face share price volatility, analyst downgrades, and investor exit. Due diligence now prioritizes cyber governance, resulting in postponed timelines or adjusted valuations for private and M&A deals.Long-term brand damage
Reputational harm does not resolve when systems are restored. It lingers in customer acquisition costs, reduced lifetime value, and increased churn, sometimes for years.Regulatory escalation
A poor response often invites ongoing oversight: follow-up audits, mandatory reporting, and heightened scrutiny of future incidents. One mismanaged breach can place an organization into a permanent high-risk category in the eyes of regulators. Also read: How Legal Support Teams Make Data Protection Policies Stronger Than IT AloneBuilding a Response That Holds Up
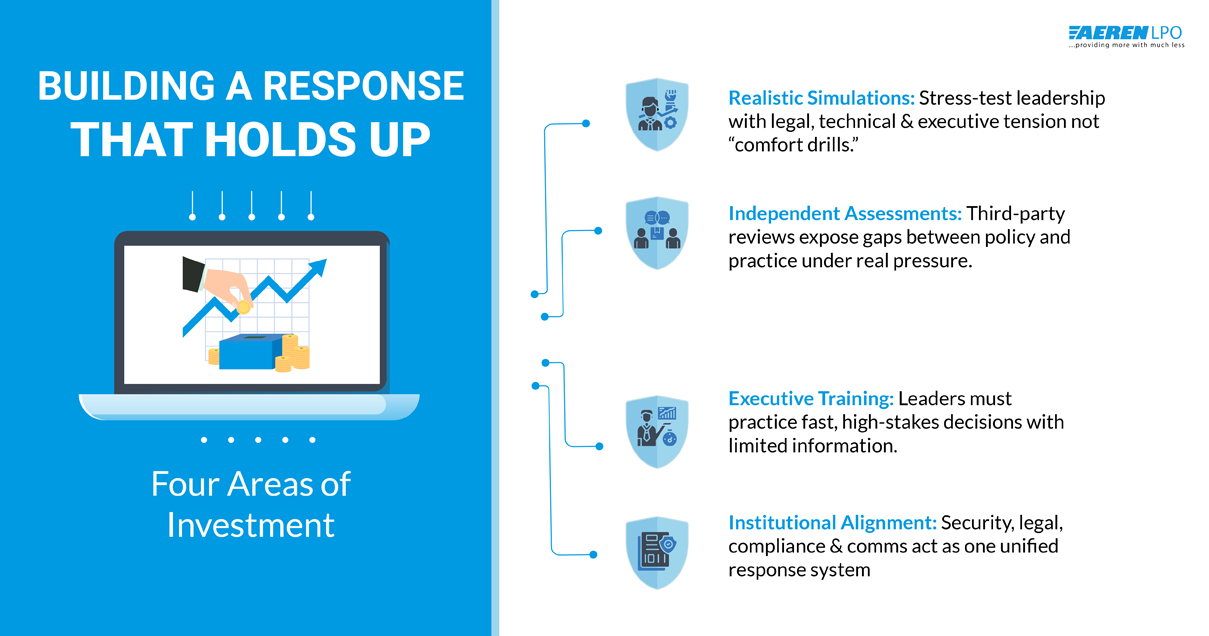
Response maturity is not achieved by publishing a plan. It is achieved by building decision discipline.
Organizations that perform well under regulatory review typically invest in four areas:
Realistic breach simulations.
Exercises must create legal, technical, and executive tension. Conflicting priorities, incomplete data, and external pressure must be part of the scenario. Comfort exercises do not prepare leadership for real disclosure decisions.
Independent readiness assessments.
Third-party reviewers test whether response structures function under stress, not whether they look coherent on paper. The gap between policy and practice is where most liability originates.
Executive decision training.
Incident plans assume senior leaders can make high-impact choices quickly and with limited information. Many have never practiced doing so. Boards and general counsel should.
True institutional alignment.
Security, legal, compliance, and communications must operate as a single response system, not as separate functions that coordinate only after a crisis begins.
Also read: The First 72 Hours of a Data Breach: What Really Matters for Legal Response Teams
Closing View
In today’s regulatory environment, a data breach is no longer judged solely as a security failure. It is judged as a test of governance.
Organizations are evaluated on how they investigated, disclosed, preserved evidence, communicated, and acted decisively. A technically well-contained breach can still become a legal and commercial disaster if these elements are mishandled.
The question is no longer whether an organization will face a breach.
It is “When that moment comes, will the data breach response demonstrate control, accountability, and maturity?”
For regulators, courts, customers, and shareholders, that is now the real measure of resilience.
That’s why at Aeren LPO, we help organizations prepare for and manage cyber incidents as legal and regulatory events, not just technical ones. If your response capability has never been tested under real scrutiny, it is worth doing so before a regulator or court does it for you.

